ow many enterprises do you know that had a disaster recovery plan including options for managing a global pandemic where all employees would be in lockdown and unable to visit their own office?
Continue readingHow a Cloud Solutions Provider Can Help Protect Your Business from Ransomware
First, we need to accept that completely preventing cybersecurity threats is unrealistic. If we’ve learned anything from the constant stream of cybersecurity breaches, it’s that threats are inevitable. The best thing to do is reduce the chance of threats and have a response plan in place for when a threat does present itself.
For instance, at WatServ, we have a collection of services that work to safeguard our clients’ cloud environments.
Our standard services (included with WatServ’s CloudOps managed service) offer:
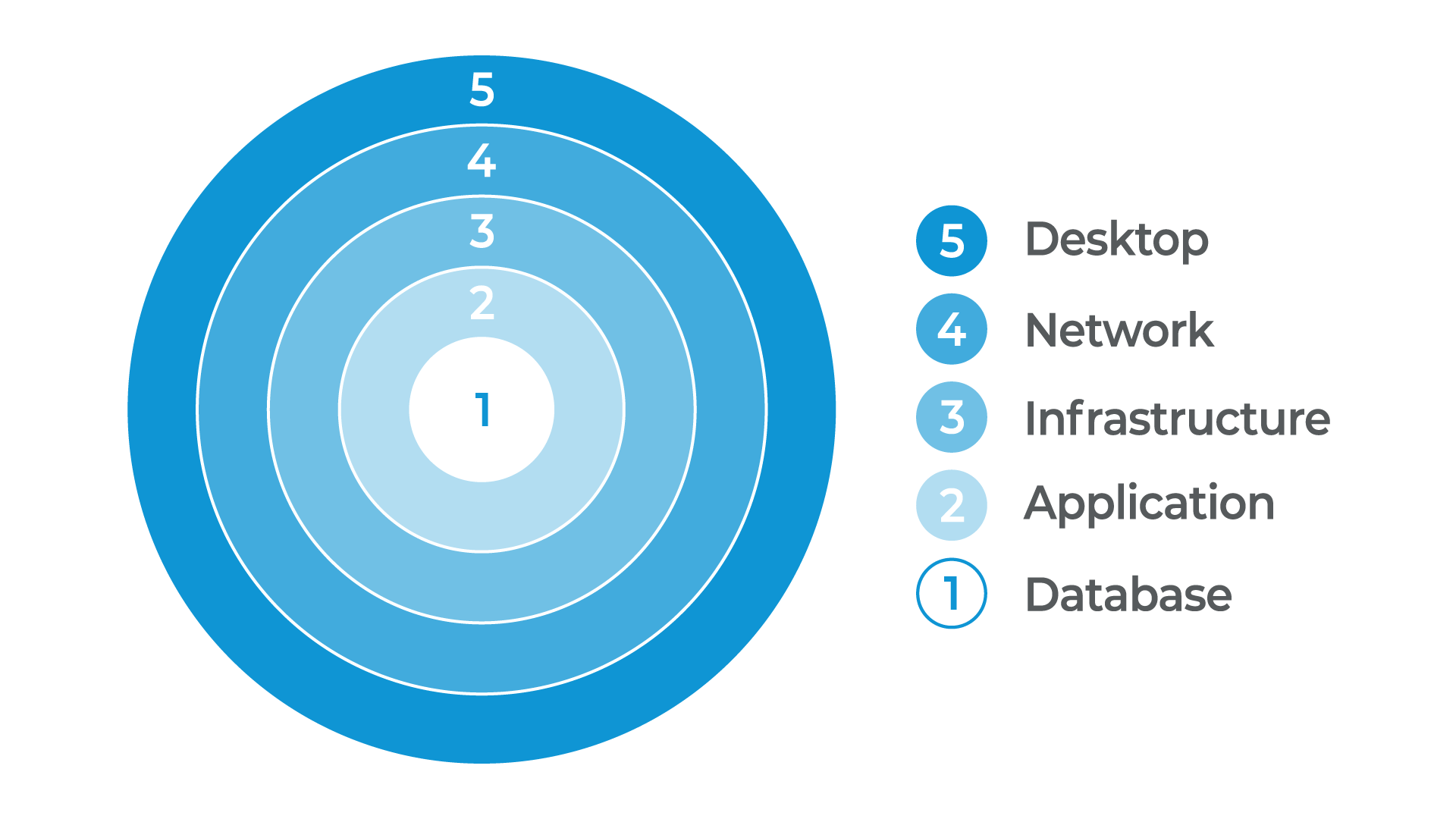
1. Foundational security pillars – based on CISA’s defense in depth concept
This approach begins with protection at the client connection. Additional layers of defense occur at the network, infrastructure, application and database levels. Each one of these layers is protected by access controls and segregation. Some examples of protective mechanisms at the layers are advanced malware protection, firewalls, multi-factor authentication, multi-tiered network segregation, password vault and access controls and reviews.
Layers of Defense